In contrast to conventional computing, the place processing is especially carried out on native servers and within the cloud, edge computing pushes functions, information, and computing energy to the sting of the Web—to cellular gadgets, sensors, and finish customers. One of many important drivers for edge computing is that the variety of gadgets linked to the Web, and the amount of information being produced by these gadgets and utilized by governments and companies, is rising far too shortly for conventional computing approaches, networks, and data-center infrastructures to accommodate.
The sting is subsequently wherever an individual is attempting to make use of a software program service. In an city surroundings, the sting may very well be a first-tier mobile supplier, a public Wi-Fi community, or a private-enterprise community. In these settings, entry to assets within the cloud is solely assumed as a result of connectivity for probably the most half is all the time accessible. Nevertheless, there are different edge environments during which connectivity to the cloud can’t be assumed, equivalent to environments during which first responders and army personnel function.
As this submit describes, the SEI is conducting utilized analysis for creating modern options, ideas, and finest practices for architecting, creating, and deploying methods to help groups working in distant places away from central computing assets the place assets are constrained. This analysis contains utilizing synthetic intelligence and machine studying (AI/ML) on the edge for improved capabilities and mission help.
We’re beginning this weblog collection referred to as “Working on the Edge” to share ideas associated to edge computing and our ongoing work and experiences architecting and creating edge methods. This weblog submit introduces ideas and challenges for Working on the Edge.
We discuss with a deprived edge surroundings during which first responders and different emergency personnel function because the humanitarian edge. It’s characterised by restricted computational assets working in unsafe situations attributable to climate occasions, seismic occasions, and even infrastructure failures, during which issues can change at a second’s discover. A extra particular characterization is proven within the callouts in Determine 1 beneath.
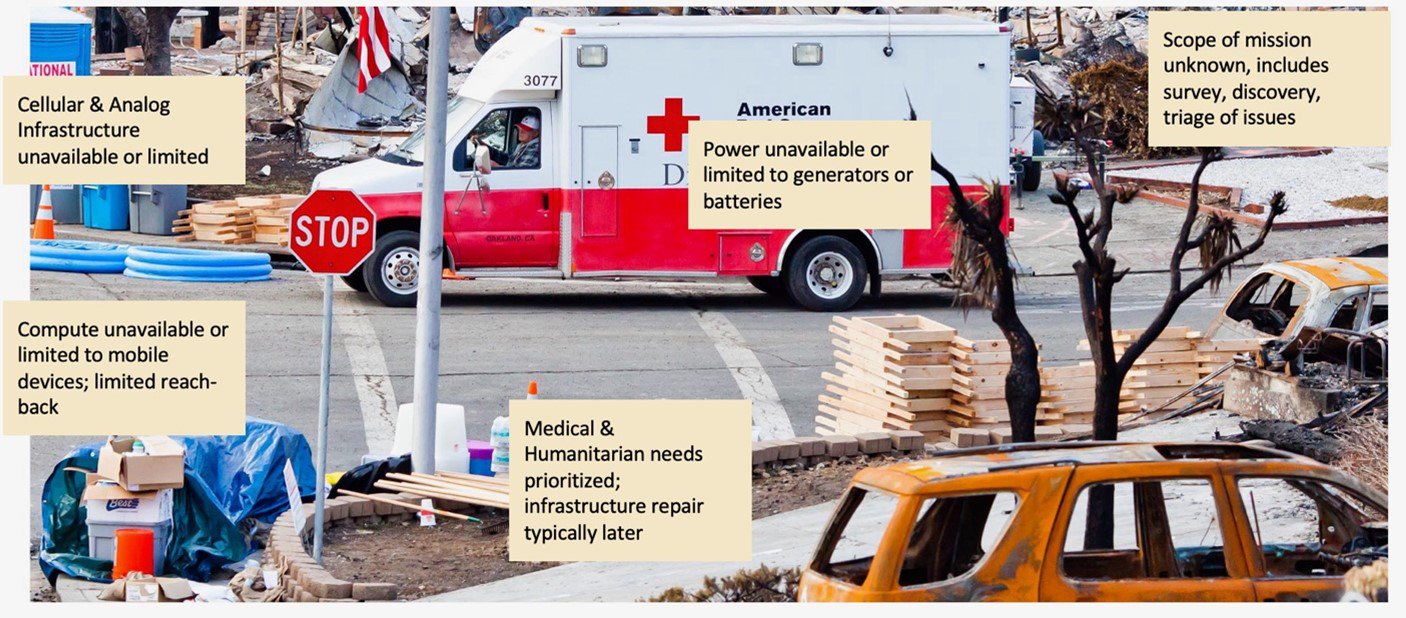
Determine 1: The Humanitarian Edge: First Responders and Humanitarian Support
First, the native community infrastructure will usually be down or have restricted connectivity, making cloud assets unavailable or unreliable. The computing assets which are accessible, usually handheld or vehicle-mounted, shall be restricted by accessible energy, which may very well be a vital concern if gasoline or different energy assets are additionally down. Then, there may be the context of the disaster; particularly in pure disasters, first responders go in with out information of the particular state of affairs on the bottom. In different phrases, there’s a discovery-and-triage course of that requires fixed shifting of assets to prioritize points as they happen, particularly when the necessity is medical.
Because of this, first responders should depend on the assets that they carry into the state of affairs, with solely a free plan of prioritization as points are recognized. Furthermore, these first responders are usually underequipped and compelled as an alternative to depend on assets provided over time or as circumstances enable. Subsequently, the humanitarian edge is a difficult surroundings of maximizing accessible assets (computational, networks, and different) on an unknown timeline, for unknown points, and having the ability to proceed operations in these environments no matter useful resource exhaustion or the person challenges of the reason for the catastrophe. Given the excessive variety of unpredictable situations, the humanitarian edge is characterised by its excessive uncertainty.
The tactical edge is the sector surroundings the place army personnel execute missions (i.e., “boots on the bottom”) and may vary from air to floor to undersea, and from city to rural settings. Determine 2 beneath reveals a canonical instance of army operations in a desert rural surroundings during which various kinds of army teams are current and performing actions.
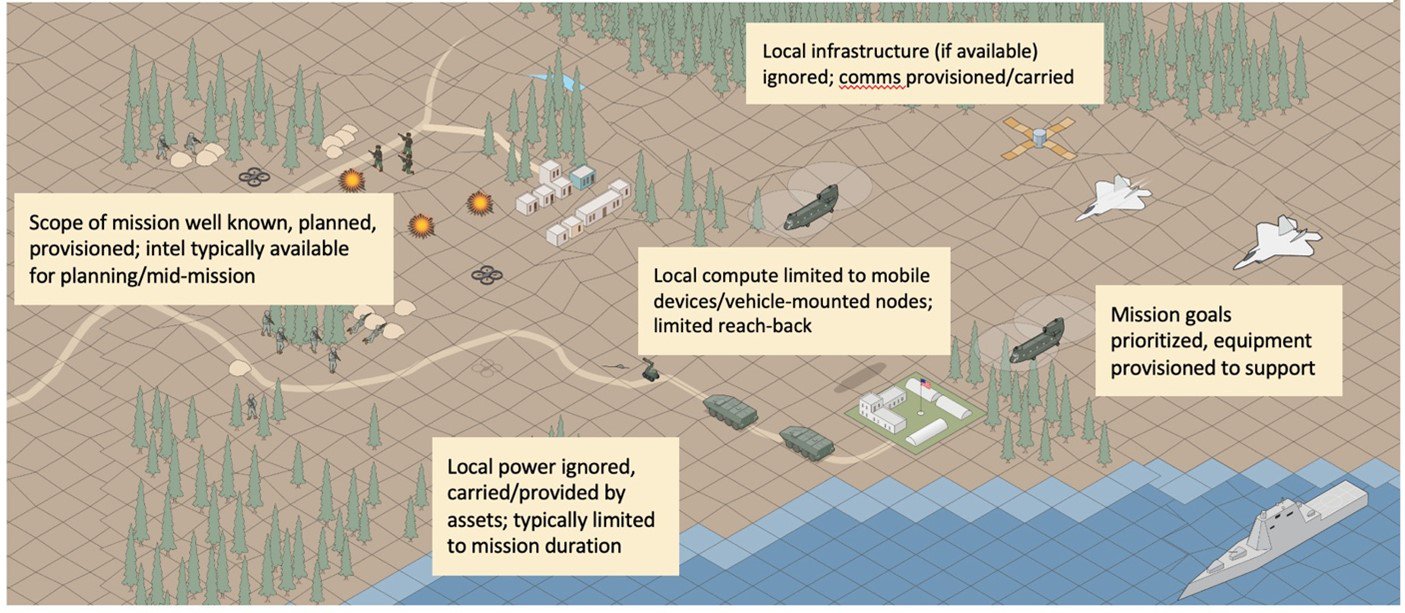
Determine 2: The Tactical Edge: Warfighters and Army Property
In these environments, warfighters are skilled to carry no matter they want with them, to make sure that they’ve the assets that they should carry out their missions. Because of this, whereas there could also be some native infrastructure and assets, they’re usually ignored in favor of army belongings. Nevertheless, the tradeoff is that army assets are sometimes restricted on the tactical edge, together with energy to computing assets to connectivity, and function in disconnected, intermittent, and low-bandwidth (DIL) community environments. Whereas assets and limitations are recognized, the danger is all the time that the character of tactical missions will lead to useful resource wants that aren’t already provisioned, leading to an obstacle. In comparison with different edge environments, such because the humanitarian edge, the tactical edge is rather more deliberate, however sadly in lots of circumstances there shall be an adversary attempting to thwart or sabotage the mission, rising the necessity for continued operation as adversaries succeed of their efforts.
Challenges Working on the Edge
Techniques which are designed to function on the humanitarian or tactical edge have to account for the next challenges intrinsic to those environments:
- restricted computing assets—Resulting from measurement, weight, and energy (SWAP) limitations, gadgets deployed to the sting are restricted of their computing assets, equivalent to CPU/GPU energy and reminiscence. Accessing cloud assets might not be doable. To as an alternative carry these capabilities to the sting, software program engineering efforts should design for distributability, which is the flexibility to separate system elements throughout a number of computing nodes.
- intermittent/denied community connectivity—Many computing capabilities are designed for “always-connected” networks and don’t deal with intermittent connections gracefully. Software program written for tactical edge nodes should be strong to deal with missions that function in areas of restricted community infrastructure, or the place communications are actively denied due to adversary efforts or pure disasters.
- restricted consideration—Each in humanitarian and tactical edge methods, operators should carry out their missions underneath extraordinarily aggravating situations with full consideration and fast decision-making, leaving little to no time to give attention to further gadgets and interfaces. Visible interfaces should be easy and uncluttered and may show solely probably the most related info. Enter gadgets must be easy, configurable, intuitive, and tactile. Info served to the operators should be centered on probably the most vital, well timed, and related facets of the mission.
High quality Attributes for Techniques on the Edge
A high quality attribute (QA) is a measurable and testable property of a system that’s used to point how effectively the system satisfies the wants of its stakeholders past the fundamental operate of the system. A system’s skill to satisfy its desired high quality attributes is considerably decided by its structure. What follows is an inventory of high quality attributes which are widespread to edge methods and that should be realized to handle the challenges of edge environments. These are listed in no explicit order; their precedence is dictated by context and what are thought-about acceptable tradeoffs.
- reliability—Reliability is the flexibility of a system to proceed operation underneath fault situations. It’s a key high quality attribute to contemplate in edge environments for continued operations. All system elements have to be resilient to failure and have restoration methods. For instance, methods must be designed to reconnect robotically with out locking up when the community disconnects. Non permanent restoration methods may very well be used, equivalent to spinning up native companies to exchange unreachable distant companies. System architects also needs to contemplate redundancy and different choices for mission-critical capabilities.
- privateness—Knowledge collected on the edge may have personally identifiable info (PII), which is an particularly vital concern in humanitarian conditions, the place the targets of saving lives and defending a person’s private info shouldn’t be mutually unique. Privateness ought to subsequently be constructed into elements that clear information earlier than sending it to the cloud, if accessible. Techniques might have to do all the processing on the sting node if PII information can’t be despatched to the cloud, due to both coverage restrictions or lack of consumer consent.
- safety—In tactical edge environments, computing nodes are working close to adversaries, who are sometimes in search of alternatives to thwart or sabotage the mission, which makes safety a paramount concern to profitable operations. If edge nodes are working on native networks, the belief should be that adversaries are monitoring the community, and all information should be encrypted. If edge nodes are working with delicate or categorized info, particular zeroization performance must be included in order that information may be shortly destroyed if the node is compromised.
- adaptability—Operations on the edge—whether or not they’re catastrophe reduction missions or energetic fight— usually include some stage of uncertainty. Edge methods should be capable to adapt to satisfy continuously shifting priorities. For edge methods to take care of uncertainty, engineers should design them with adaptability in thoughts. Edge software program ought to be capable to adapt throughout operations to each the information it’s processing and the kind of computation it’s executing. An operator might not have the eye to regulate the software program on-the-fly, so organising particular modes for various phases of the mission can present flexibility with simplicity for the operator.
- scalability—Units on the edge are sometimes small and specialised. A whole lot or hundreds of nodes may have to find one another, join, and share information, resulting in scalability challenges. These nodes are sometimes heterogenous, together with completely different {hardware} and software program components. As well as, tactical and humanitarian environments usually have a number of entities—equivalent to native populations or non-governmental organizations—with distinct gadgets and computing nodes. Ensuing scalability challenges embody get all of the nodes to interoperate, course of all the information, and decrease load on the community.
- interoperability—Given the breadth of organizations and gadgets performing duties on the edge, additionally it is vital to construct for interoperability, which is the diploma to which two or extra methods can usefully change significant info by way of interfaces. Making the most of messaging middleware can ease the method of methods integration. Utilizing cross-platform network-serialization libraries, equivalent to protocol buffers and interfaces that clearly outline codecs, may help stop data-formatting errors.
- survivability—Given the sting challenges, a system should be capable to survive them. Survivability implies that the system ought to proceed to function in addition to doable regardless of harm to {hardware} (computing assets, energy, or networking) or the consumer. Survivability is usually associated to the reliability problem. Nevertheless, the important thing distinction is that reliability is a few system adapting to a difficult surroundings to keep up functionality. In distinction, survivability is about acceptance of bodily useful resource loss and sustaining functionality in addition to doable with the assets accessible, which is the place the notion of cutting down comes into play. Given a bodily lack of computing assets, energy, or networking, the system ought to adapt and keep as a lot functionality as doable, ideally prioritizing capabilities primarily based on the present wants of the consumer.
- distributability—Given the restricted functionality of edge gadgets, a system on the edge shall be most succesful if it takes benefit of nodes working collectively. Distributability implies that a system can function throughout a number of edge nodes in live performance. The thought is that, given the belief that gadgets within the edge surroundings could have restricted assets, elevated functionality is likely to be realized by distributing computation among the many gadgets which are accessible. Implementing capabilities as microservices is a perfect architectural tactic to help this high quality attribute. This method includes creating a set of standardized microservices and deploying them throughout a number of gadgets on a domestically linked community, relying on the wants of the second. On this approach, the assets which are at the moment accessible can collaborate on duties, releasing the consumer from being restricted by the assets that they’ve bodily available, particularly if their private gadgets are broken or in any other case unavailable as a result of challenges of the surroundings.
- openness—Given the challenges on the edge and the historic mixture of software program and gadgets which are supplied to troopers and first responders, we can’t count on that one vendor or group will clear up all of those challenges. Openness implies that the system should use well-defined, open, and well-supported interfaces and platforms in order that any group with an efficient software program or {hardware} resolution can simply combine with the system. It’s our expertise that relating to edge environments, completely different events present items of the answer and never a full resolution. As such, enabling simple integration of elements and utilizing well-defined interfaces turns into a vital characteristic of any structure. In these efforts, the aptitude to combine in days or even weeks vs. requiring weeks or months is essential.
Context and Different Facets of Edge Computing
The challenges of working in edge environments change into a part of the context for architecting edge methods and likewise present enter for prioritization of high quality attributes. For instance, in a tactical edge system, safety and distributability is likely to be the top of the range attributes if delicate information is being collected and should be processed on the edge. In a humanitarian edge system, the top of the range attributes is likely to be interoperability and openness if a number of organizations are coming collectively to offer support. Along with context, the system is likely to be constrained by different elements, equivalent to current legacy methods, heterogeneity of recent and previous {hardware}, and different vital system attributes that we haven’t lined right here, together with latency, maintainability, and evolvability.
Future posts in our collection will give attention to different facets of edge computing, equivalent to utilizing AI/ML elements as a part of edge methods, service administration and deployment, environment friendly information processing, and safety when Web of Issues (IoT) gadgets are concerned.
To be taught extra about our work on this space, please see the extra assets listed beneath.

