Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
[ad_1]
With the latest demise of a number of widespread “proxy” providers that allow cybercriminals route their malicious site visitors by way of hacked PCs, there may be now one thing of a provide chain disaster gripping the underbelly of the Web. Compounding the issue, a number of remaining malware-based proxy providers have chosen to dam new registrations to keep away from swamping their networks with a sudden inflow of consumers.

Final week, a seven-year-old proxy service referred to as 911[.]re abruptly introduced it was completely closing after a cybersecurity breach allowed unknown intruders to trash its servers and delete buyer knowledge and backups. 911 was already akin to crucial infrastructure for a lot of within the cybercriminal group after its prime two rivals — VIP72 and LuxSocks — closed or had been shut down by authorities over the previous 10 months.
The underground cybercrime boards are actually awash in pleas from people who find themselves desperately looking for a brand new provider of ample, low-cost, and reliably clear proxies to restart their companies. The consensus appears to be that these days are actually over, and whereas there are lots of smaller proxy providers remaining, few of them on their very own are able to absorbing wherever close to the present demand.
“Everyone is in search of an alternate, bro,” wrote a BlackHatForums person on Aug. 1 in response to considered one of many “911 different” dialogue threads. “Nobody is aware of an equal different to 911[.]re. Their service by way of worth and accessibility in comparison with different proxy suppliers was unmatched. Hopefully somebody comes with a terrific different to 911[.]re.”
Among the many extra incessantly advisable options to 911 is SocksEscort[.]com, a malware-based proxy community that has been in existence since not less than 2010. Right here’s what a part of their present homepage seems to be like:
The SocksEscort residence web page says its providers are excellent for individuals concerned in automated on-line exercise that usually leads to IP addresses getting blocked or banned, akin to Craigslist and relationship scams, search engine outcomes manipulation, and on-line surveys.
However confronted with a deluge of latest signups within the wake of 911’s implosion, SocksEscort was among the many remaining veteran proxy providers that opted to shut its doorways to new registrants, changing its registration web page with the message:
“As a result of uncommon excessive demand, and heavy load on our servers, we needed to block all new registrations. We received’t be capable of help our proxies in any other case, and shut SocksEscort because of this. We’ll resume registrations proper after demand drops. Thanks for understanding, and sorry for the inconvenience.”
In line with Spur.us, a startup that tracks proxy providers, SocksEscort is a malware-based proxy providing, which suggests the machines doing the proxying of site visitors for SocksEscort clients have been contaminated with malicious software program that turns them right into a site visitors relay.
Spur says SocksEscort’s proxy service depends on software program designed to run on Home windows computer systems, and is presently leasing entry to greater than 14,000 hacked computer systems worldwide. That could be a far cry from the proxy stock marketed by 911, which stood at greater than 200,000 IP addresses for hire only a few days in the past.
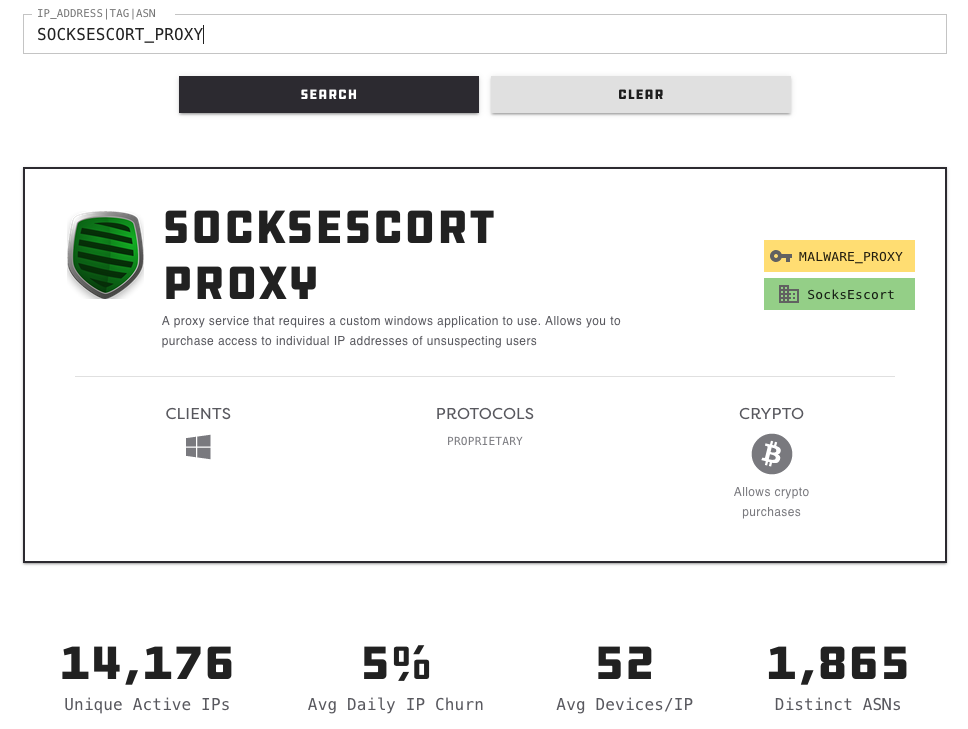
Picture: Spur.us
SocksEscort is what’s often called a “SOCKS Proxy” service. The SOCKS (or SOCKS5) protocol permits Web customers to channel their Internet site visitors by way of a proxy server, which then passes the data on to the supposed vacation spot. From a web site’s perspective, the site visitors of the proxy community buyer seems to originate from a rented/malware-infected PC tied to a residential ISP buyer, not from the proxy service buyer.
These providers can be utilized in a official method for a number of enterprise functions — akin to value comparisons or gross sales intelligence — however they’re massively abused for hiding cybercrime exercise as a result of they make it troublesome to hint malicious site visitors to its authentic supply.
The disruption at 911[.]re got here days after KrebsOnSecurity revealed an in-depth take a look at the long-running proxy service, which confirmed that 911 had a historical past of incentivizing the set up of its proxy software program with out person discover or consent, and that it truly ran a few of these “pay-per-install” schemes by itself to ensure a gradual provide of freshly-hacked PCs.
That story additionally confirmed as soon as once more that the people who find themselves constructing and leasing these botnets are surprisingly simple to establish in actual life, significantly on condition that they function malware-based anonymity providers that allow a substantial amount of cybercrime exercise.
Such was the case once more with SocksEscort. Hilariously, the widespread hyperlink that uncovered the real-life identities of the individuals operating this SOCKS service was that all of them labored for a similar on-line shoe retailer.
SocksEscort[.]com was initially registered to the e-mail handle “[email protected],” which based on DomainTools.com was used to register a handful of associated domains, together with its earlier incarnation — super-socks[.]biz. Cached variations of the positioning present that in 2010 the software program which powers the community was produced with a copyright of “Escort Software program.”
Tremendous-socks[.]biz got here on-line across the identical time as one other area registered to that “michdomain” e-mail: ip-score[.]com, which quickly grew to become shorthand on a number of cybercrime boards for a service that would inform guests whether or not their Web handle — or extra exactly, the proxy they had been utilizing — was flagged by any safety software program or providers as compromised or malicious.
IP-score provided a income sharing program for web sites that selected to embed its IP-scoring code, and the copyright on that userbar program was “Indignant Coders.”

A duplicate of ip-score.com, as listed by Archive.org.
A evaluate of the Web addresses traditionally utilized by Tremendous-socks[.]biz and SocksEscort[.]com reveals that these domains at varied occasions through the years shared an Web handle with a small of different domains, together with angrycoders[.]internet, iskusnyh[.]professional, and kc-shoes[.]ru.
Cached copies of angrycoders[.]internet from the Wayback Machine don’t reveal a lot about this explicit group of irate programmers, however a search on the area brings up a number of now-dormant listings for an Indignant Coders primarily based in Omsk, a big metropolis within the Siberian area of Russia. The area was registered in 2010 to an Oleg Iskushnykh from Omsk, who used the e-mail handle [email protected].
In line with Constella Intelligence [currently an advertiser on KrebsOnSecurity], Oleg used the identical password from his [email protected] account for a slew of different “iboss” themed e-mail addresses, considered one of which is tied to a LinkedIn profile for an Oleg Iskhusnyh, who describes himself as a senior net developer residing in Nur-Sultan, Kazakhstan.
Iskusnyh’s Github profile exhibits he has contributed code to quite a lot of on-line payment-related applied sciences and providers, together with Ingenico ePayments, Swedbank WooCommerce, Mondido Funds, and Reepay.
The assorted “iboss” e-mail accounts seem to have been shared by a number of events. A search in Constella’s database of breached entities on “[email protected]” reveals somebody utilizing the identify Oleg Iskusnyh registered a web based profile utilizing a cellphone quantity in Bronx, New York. Pivoting on that cellphone quantity — 17187154415 — reveals a profile uncovered within the breach at gross sales intelligence agency Apollo with the primary identify “Dmitry” who used the e-mail handle [email protected].
That e-mail is linked to a LinkedIn profile for a Dmitry Chepurko in Pavlodar, Kazakhstan. Chepurko’s resume says he’s a full stack developer, who most lately labored within the Omsk workplaces of a German shoe firm referred to as KC Sneakers (the aforementioned kc-shoes.ru]. Chepurko’s resume says earlier than that he labored on his personal for a decade utilizing the freelancing platform Upwork.
The Upwork profile listed in Chepurko’s LinkedIn C.V. is not energetic. However that very same now-defunct Upwork account hyperlink continues to be listed because the profile of a “Dmitry C.” in an UpWork profile web page for the Indignant Coders workforce in Omsk, Russia.
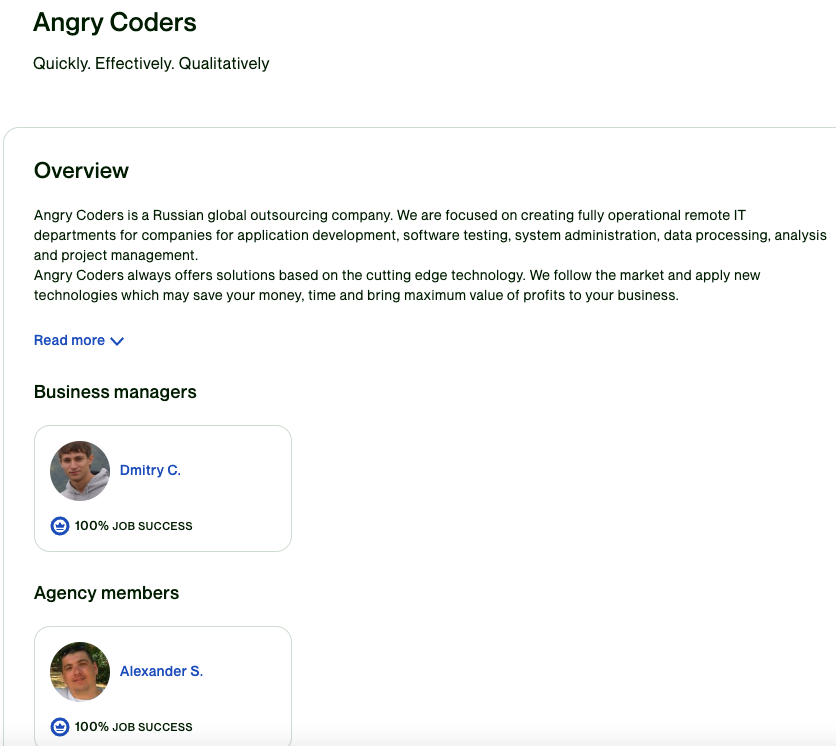
The UpWork profile web page for the Indignant Coders programming workforce from Omsk, RU.
Who’s the “Alexander S.” listed above below the “Company members” heading within the Upwork profile for Indignant Coders? Historic DNS information from Farsight Safety present angrycoders.internet previously included the subdomain “smollalex.angrycoders[.]internet”.
A easy Web search on “kc-shoes” reveals a Github account for a person from Omsk with the primary identify Alexander and the account identify “Smollalex.” Alexander’s Github account signifies he has contributed code to the kc-shoes web site as effectively.
Constella’s service exhibits that “Smollalex” was a favourite deal with chosen by an Alexandr Smolyaninov from Omsk. The Smollalex Github account associates this particular person with an organization in Omsk that sells elements for oil and fuel pipelines.
That sneakers are apparently the widespread hyperlink among the many Indignant Coders accountable for SocksEscort is doubly amusing as a result of — not less than based on the posts on some cybercrime boards — one huge motive individuals flip to those proxy providers is for “shoe botting” or “sneaker bots,” which refers to using automated bot packages and providers that help within the speedy acquisition of limited-release, highly-sought-after designer athletic sneakers that may then be resold at big markups on secondary markets.
It’s not clear if the Indignant Coders workforce members stay affiliated with SocksEscort; none of them responded to requests for remark. There have been sure connections made clear all through the analysis talked about above that the Indignant Coders outsourced a lot of the promotion and help of their proxy service to programmers primarily based in India and Indonesia, the place apparently a big chunk of its clients presently reside.
Additional studying:
July 29, 2022: 911 Proxy Service Implodes After Disclosing Breach
July 28, 2022: Breach Exposes Customers of Microleaves Proxy Service
July 18, 2022: A Deep Dive Into the Residential Proxy Service ‘911’
June 28, 2022: The Hyperlink Between AWM Proxy & the Glupteba Botnet
June 22, 2022: Meet the Directors of the RSOCKS Proxy Botnet
Sept. 1, 2021: 15-Yr-Outdated Malware Proxy Community VIP72 Goes Darkish
[ad_2]