Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
[ad_1]
When incrementally changing legacy programs with new ones, it is not going to be
potential to cleanly isolate the brand new world from the previous.
A Transitional Structure requires that the brand new world supplies information (or
another interplay) with the intention to “preserve the lights on”.
When that is the case the brand new system should meet some current (typically
implicit) contract, and so the brand new system should develop into a Legacy Mimic.
By exploring the legacy system’s technical structure and goal
structure imaginative and prescient, and understanding the prevailing and to-be
enterprise processes, seams may be found and exploited permitting the
drawback to be damaged up into components.
The Legacy Mimic sample is an enabler for these seams, and creates choices
for, and is an implication of, totally different sequencing approaches.
A Legacy Mimic typically realises the Anti-Corruption Layer sample from Eric
Evans’s Area Pushed Design e book.
There are comparable forces at play because the Anti-Corruption Layer‘s intent is to:
Create an
isolating layer to supply shoppers with performance when it comes to their very own
area mannequin. The layer talks to the opposite system via its current
interface, requiring little or no modification to the opposite system.
Internally the layer interprets in each instructions as needed between the
two fashions.
Just like an Anti-Corruption Layer a Legacy Mimic’s implementation will usually use
Companies, Adapters, Translators and Facades.
There are a minimum of 2 kinds of mimics that we generally see, and are most
simply defined when it comes to offering or consuming providers.
A Service Offering Mimic will encapsulate a brand new implementation behind a
legacy interface. Legacy elements will be capable to work together with it
utilizing the legacy interface and never know that they’re collaborating with
that new implementation.
A Service Consuming Mimic will collaborate with the legacy programs that
haven’t but been changed utilizing their current legacy interfaces. Once more
this interplay might be clear to the previous system.
To additional illustrate these several types of mimics this determine exhibits
a monolythic legacy system that helps 3 enterprise processes – Gross sales,
Logistics and Enterprise Efficiency.
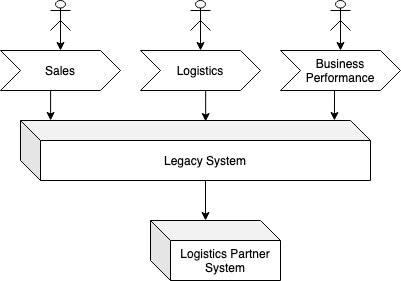
An choice being thought-about is to make use of the Extract Worth Streams for
the Logistics functionality. Doing so might lead to a transitional
structure like:
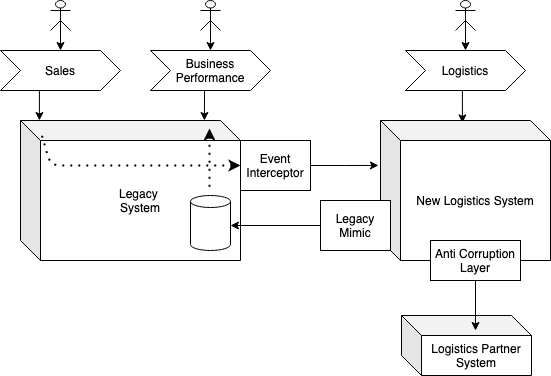
To ensure that the brand new logistics system to course of the achievement of
gross sales, Occasion Interception is proposed. On this instance the Occasion Interceptor
is an instance of a Service Offering Mimic – it’s conforming to the
legacy interface (consumption of legacy occasions).
To ensure that the Enterprise Efficiency course of to proceed to perform, once more
the usage of the Legacy Mimic sample is proposed, however this time as a Service
Consuming Mimic. It’s going to replicate the required logistics metrics into the
legacy reporting database (conforming to the legacy database’s schema and
semantics).
Each of those elements is not going to endure in inside the goal structure
of the system – they’re transitional.
The prevailing Logistics Associate System should nonetheless be built-in with, so
an Anti-Corruption Layer is utilized by the brand new Logistics system. As this can
endure it’s not thought-about a mimic (or transitional), however the creation
of the Anti-Corruption Layer is used so that the area mannequin of the brand new
Logistics System is just not compromised by the mannequin utilized by that exterior
system.
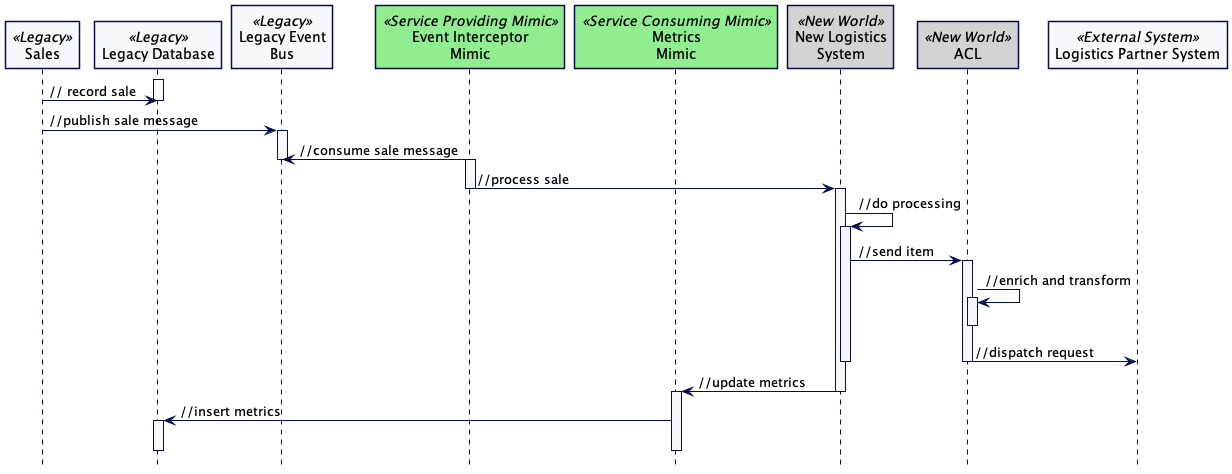
[ad_2]